Introduction
In today’s world, staying safe online and keeping your business private is super important. That’s where the Tor Browser comes in it’s like a special door to the internet that helps you stay hidden and secure. Unlike regular browsers, Tor gives you more anonymity, letting you visit websites and even the dark web without being easily tracked. It’s an open-source tool, meaning anyone can check how it works, and it’s available on many devices.
What is Tor Browser?
Think of Tor Browser as your bodyguard for the internet. It stands for “The Onion Router,” and it’s made to give you online privacy. The cool thing about Tor is how it uses something called onion routing. Imagine your internet traffic wrapped in layers like an onion – each layer hides your location and what you’re doing from prying eyes. This makes it tougher for anyone, like your internet company or even governments, to snoop on you. With Tor Browser, you get anonymous browsing and protection against traffic analysis.
History of Tor
Tor’s story starts way back in the 1990s with the U.S. Navy, who wanted a safe way to communicate. Some smart folks at the Naval Research Laboratory came up with the idea of onion routing to hide where messages were coming from and going. Later on, in 2002, it became a public project, and people from all over the world started working on it. Tor got its name from “The Onion Router” because of those layers of security. It went from a government project to a tool for everyone who cares about censorship circumvention, digital privacy, and staying anonymous online. Now, the Tor Project, a non-profit, keeps Tor running and makes sure it stays a champion for internet freedom.
Importance of Online Privacy
These days, online privacy is a big deal. It’s easy for our personal info to get out there, which can lead to problems like identity theft or even being watched by the government. Online privacy is a basic right it lets us be ourselves and make our own choices. When we can control what info we share, we can trust each other more and feel safer online. Using Tor Browser is one way we can take charge of our digital security and keep our online lives private. Secure internet browsing is more important than ever to keep our data safe.
Getting Started with Tor Browser
So, you’re ready to dive into the world of anonymous browsing with Tor Browser? Great! Here’s a simple guide to get you up and running, whether you’re a complete beginner or a seasoned tech enthusiast. We will cover installation, configuration, and first use. The Tor Browser provides the highest level of anonymity.
Step-by-Step Guide to Installing Tor Browser
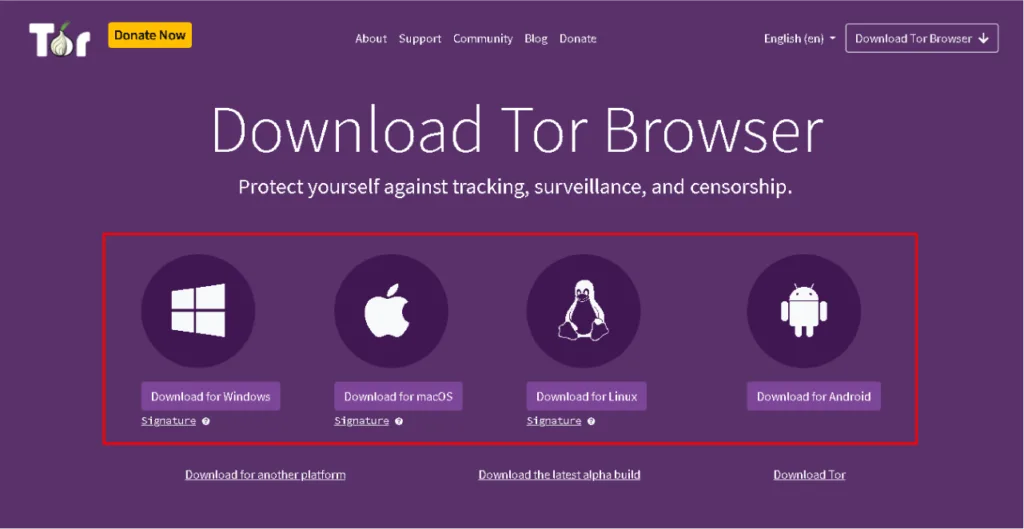
Getting Tor Browser Download is straightforward. Just follow these steps:
- Visit the official Tor Project website: Head over to torproject.org. Make sure you’re on a genuine site to avoid downloading fake or compromised versions.

- Download the correct version: You’ll see options for Windows, macOS, Linux, and Android. Choose the one that matches your device. Tor Browser is multi-platform, ensuring almost everyone can access secure internet browsing.
- Run the installer:
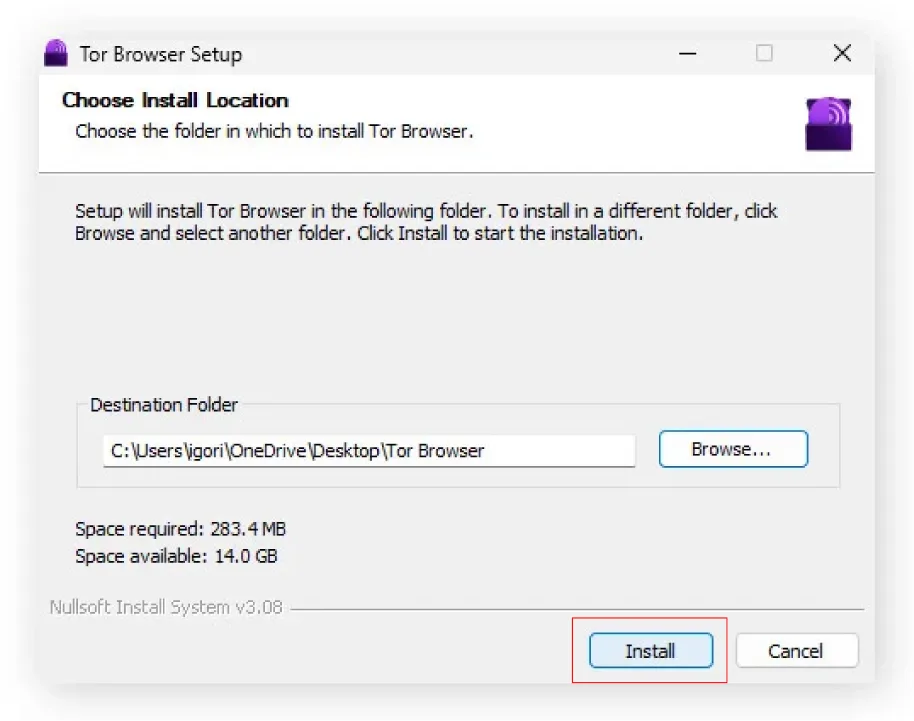
- Windows: Double-click the downloaded
.exefile and follow the on-screen instructions. You’ll be asked where to install Tor Browser. Sticking with the default location is bestunless you have a specific reason for choosing otherwise. - macOS: Open the downloaded
.dmgfile and drag the Tor Browser icon to your Applications folder. - Linux: The process varies depending on your distribution, but generally involves extracting the downloaded archive and running the Tor Browser setup script.
- Android: Find it in the Google Play Store, download and install it.
- Windows: Double-click the downloaded
- Complete the installation: Once the files are extracted and installed, you should have a Tor Browser icon on your desktop or in your applications menu.
Initial Setup and Configuration Options
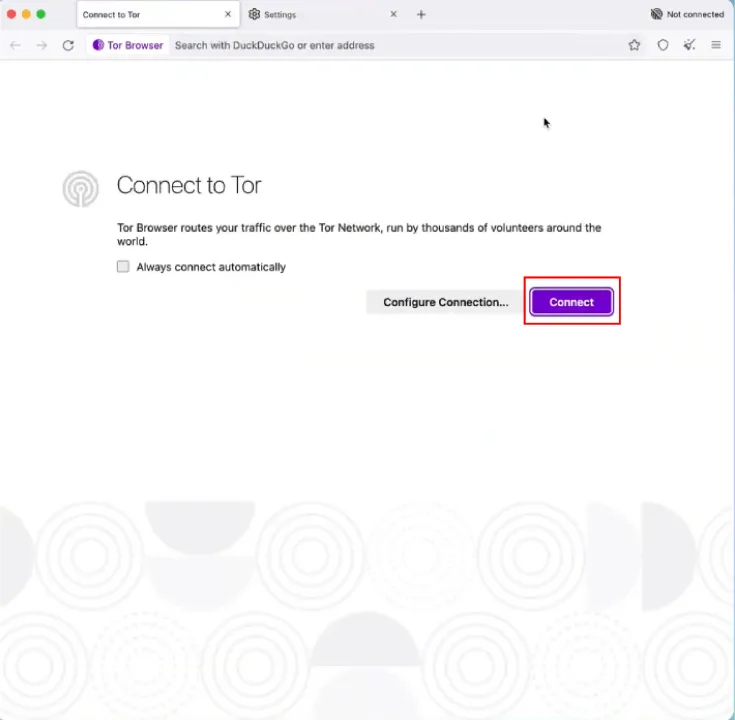
When you launch Tor Browser for the first time, you’ll see a window with a few options:
- Connect: This is the simplest option. If you’re in a country with unrestricted internet access, clicking “Connect” will automatically establish a connection to the Tor network.
- Configure: If you’re in a country where the Tor network is blocked, or if you use a proxy, you’ll need to configure your connection. This is where Tor Bridges comes in.
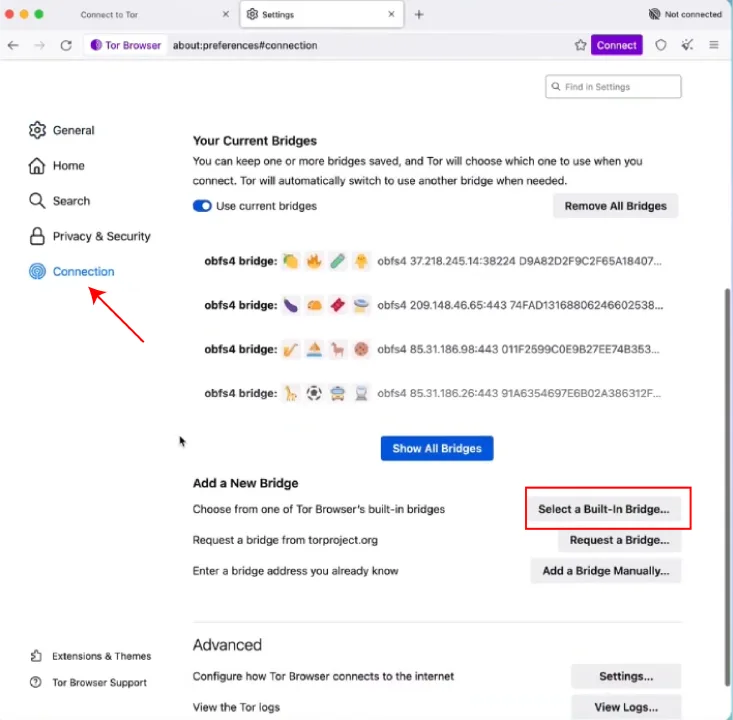
- Bridges: Bridges are encrypted tunnels that help you bypass censorship. To use a bridge, select “Configure,” then “Bridges,” and choose one of the built-in bridge options or enter a custom bridge address.
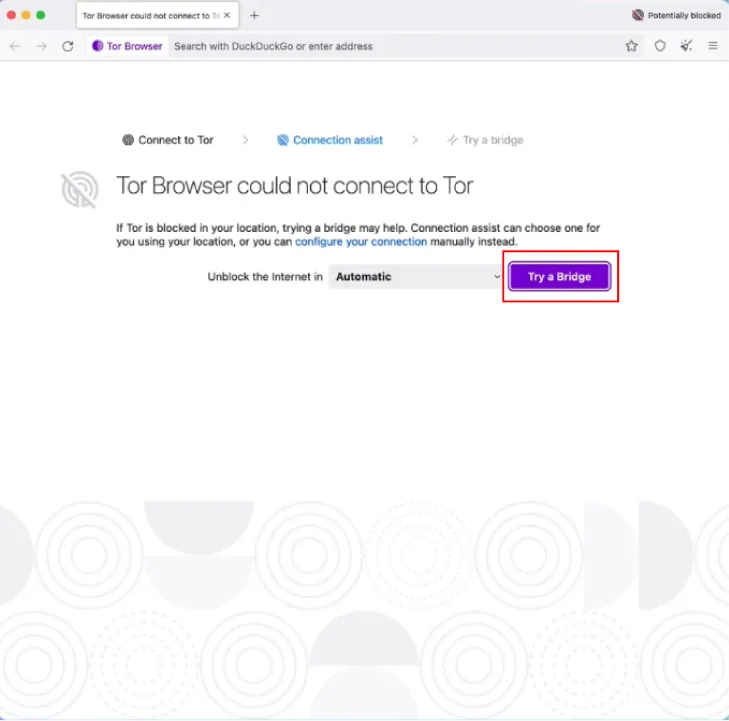

- Proxy Settings: If you use a proxy server, enter your proxy details in the configuration window.
How to Start Using Tor Browser for the First Time
Once you’ve connected to the Tor network, you’re ready to start anonymous web surfing. Here are a few tips for your first use:
- Familiarize yourself with the interface: The Tor Browser interface is similar to Firefox, but with a few key differences. Look for the “onion” icon in the toolbar, which indicates your connection status.
- Check your IP address: Visit a website like check.torproject.org to confirm that your IP address is being anonymized.
- Adjust your security level: Tor Browser offers three security levels: Standard, Safer, and Safest. You can adjust these settings by clicking the “onion” icon and selecting “Security Settings”.
- Standard: All website features are enabled.
- Safer: JavaScript is disabled on non-HTTPS sites.
- Safest: JavaScript is disabled by default, and some fonts and images may be disabled to reduce the risk of traffic analysis protection.
- Browse carefully: While Tor Browser provides enhanced anonymity, it’s important to browse responsibly. Avoid logging into personal accounts, downloading torrents, or enabling browser plugins, as these can compromise your anonymity.
- Access .onion sites: To access .onion sites (dark web sites), simply enter the address in the address bar. Keep in mind that these sites can be risky, so proceed with caution. The Tor Browser is automatically connected to the Tor network and will place all your requests through it while ensuring anonymity. Tor Browser takes online privacy to an extreme. With Tor Browser, you can achieve a high level of digital security and online anonymity.
Features of Tor Browser
The Tor Browser is a modified version of Firefox designed to provide secure and anonymous internet access. It is a vital tool for users seeking online privacy, anonymity, and protection against surveillance and censorship. The Tor Browser anonymizes your web traffic and offers a range of features that enhance your online security and anonymity. Below are its features;
1. Hiding Your IP Address
The Tor Browser conceals your IP address, making it superlatively difficult for websites and online trackers to identify your location. It achieves this by routing your internet traffic through a network of volunteer-run servers known as relays. When you use the Tor Browser, your traffic enters the Tor network and is directed randomly through multiple relays, each adding a layer of encryption. This process makes it virtually impossible for anyone to trace your online activity back to your IP address. Hiding your IP address helps minimize online tracking and prevent targeted advertising.
2. Anonymizing Web Traffic via Onion Routing
Tor employs onion routing, a technique that encrypts your data in multiple layers, like an onion. Each relay in the Tor network peels off a layer of encryption to forward the traffic to the next relay. This process conceals the data’s source and destination, providing robust protection against traffic analysis. The Tor network consists of entry, middle, and exit relays. The entry relay receives your initial request, the middle relays forward the traffic, and the exit relay sends the traffic to its final destination. Because of this peer-to-peer (P2P) overlay network, your ISP can only see that you are connecting to a Tor entry node, not your actual destination.
3. Automatic Clearing of Browsing History and Cookies
The Tor Browser is designed to automatically clear your browsing history and cookies when you close the browser. This ensures that no data is stored locally on your computer, preventing anyone from accessing your browsing activity. Tor Browser starts in Private Browsing mode, and site data (cookies, localStorage, indexedDB, window.cache, etc) are not engineered even with Firefox to be retained when the session ends. You can manually clear your browsing history, cache, and cookies through the browser’s settings. By default, Tor Browser does not maintain any cookies that contain your browsing history. The cookies from the websites are valid only for a single session until you exit TOR.
4. Resisting Browser Fingerprinting
Tor Browser resists browser fingerprinting, a technique used by websites to identify and track users based on their browser configuration. To combat fingerprinting, Tor standardizes various aspects of its browser to make all users appear the same. This includes settings such as screen resolution, operating system, and browser plugins. By making all Tor users appear identical, it becomes extremely difficult for websites to create unique fingerprints and track individual users.
5. Preventing Tracking by Third-Party Sites
The Tor Browser prevents tracking by third-party sites by blocking trackers and isolating cookies. This limits the amount of data third-party companies can collect about you and your browsing habits. By masking your IP address and online activity, Tor makes it more challenging for companies and websites to build a comprehensive profile about you. Tor makes it difficult for advertisers and trackers to follow you across the web.
6. Accessing .onion Services on the Dark Web
Tor Browser allows access to .onion services, also known as hidden services, on the dark web. These services are only accessible through the Tor network and provide a secure and private way to communicate and share information. To access an .onion address, you need to enter it into the Tor Browser address bar. Onion services offer end-to-end encryption and anonymity, protecting both the user and the service from surveillance
Advanced Usage
The Tor Browser provides robust anonymity and privacy for regular use. However, advanced users can further enhance their security and anonymity through specific configurations and techniques. These include changing identity, using bridges, and adjusting security settings. Mastering these advanced techniques allows users to maximize the Tor Browser’s potential for censorship circumvention and mass surveillance circumvention.
1. Changing Identity
The Tor Browser has a “New Identity” feature that allows you to change your exit relay and effectively create a new online identity. This is useful if you believe your current Tor circuit has been compromised or if you want to start a new browsing session with a clean slate. To change your identity, simply click the “New Identity” button in the Tor Browser toolbar. This will close all your open tabs and windows, clear your browsing history and cookies, and establish a new Tor circuit with a different exit relay. Using this feature helps to protect against end-to-end correlation. Changing your identity periodically is superlatively effective to prevent tracking and maintain a high level of anonymity.
2. Using Bridges
Bridges are Tor relays that are not publicly listed. They act as entry points to the Tor network, helping users bypass internet censorship in countries where Tor is blocked. Using bridges conceals the fact that you are connecting to the Tor network, making it harder for censors to block your access. To use bridges, you need to configure Tor Browser to use them. You can obtain bridge addresses from the Tor Project website or through other trusted sources. Once you have the bridge addresses, enter them into the Tor Browser settings under the “Bridges” section. Bridges are especially useful in countries with strict internet censorship. Bypassing Tor network blocks requires bridges to mask your connection.
3. Configuring Security Settings
Tor Browser offers several security settings that you can adjust to maximize your protection. These settings are accessible through the Tor Browser’s security preferences.
- Security Level: The Tor Browser offers three security levels: Standard, Safer, and Safest. The “Standard” setting enables all browser features and allows websites to function as intended. The “Safer” setting disables JavaScript on non-HTTPS sites and some HTML5 features to reduce the attack surface. The “Safest” setting disables JavaScript completely, which can break some websites but provides the highest level of security.
- HTTPS Everywhere: Ensure that the “HTTPS Everywhere” extension is enabled. HTTPS Everywhere automatically encrypts your communication with websites, protecting you from eavesdropping.
- NoScript: The NoScript add-on is built in to Tor Browser, even though JavaScript is allowed by default at the Standard security level.
- Update Regularly: Keep your Tor Browser up to date. Regular updates include security patches and new features that protect you from the latest threats.
Adjusting security settings for maximum protection ensures that your online activities remain private and secure. Configuring security settings is superlatively important for protecting data and preventing surveillance.
Best Practices for Using Tor
While the Tor Browser offers a high level of anonymity and privacy, it’s crucial to follow best practices to maximize your security and avoid common mistakes. Understanding the dos and don’ts, using VPNs strategically, and staying vigilant online will help you maintain a secure and anonymous browsing experience. Following these guidelines ensures that you leverage Tor’s capabilities effectively for censorship circumvention and protecting your digital rights.
Dos and Don’ts: Common mistakes to avoid
To ensure optimal anonymity and security while using Tor, avoid these common mistakes:
- Don’t use Tor for online shopping or banking: Tor is not designed for activities that require sensitive personal or financial information. The Tor network’s anonymity can complicate or block financial transactions.
- Don’t disable Tor’s security features: Tor’s default security settings are carefully configured to provide the best balance of security and usability. Disabling these features can weaken your anonymity and make you vulnerable to attacks.
- Don’t use Tor to access illegal content: Engaging in illegal activities while using Tor does not make you immune to prosecution. In fact, it may draw unwanted attention to yourself.
- Don’t trust every website you visit: Exercise caution when visiting websites, especially on the dark web. Be wary of phishing scams, malware, and other malicious content.
- Don’t use browser plugins or extensions: Browser plugins and extensions can compromise your anonymity by revealing your IP address or other identifying information.
- Don’t use Tor for high-bandwidth activities: Tor is not designed for high-bandwidth activities such as downloading large files or streaming video. These activities can slow down the Tor network for other users.
- Don’t assume you’re completely anonymous: Tor provides a high level of anonymity, but it is not foolproof. There are techniques for tracking Tor users, such as end-to-end correlation.
Avoiding these mistakes helps ensure that you maintain a high level of online privacy and security while using the Tor Browser. Avoiding these mistakes is superlatively important to protect yourself.
Enhancing Security with VPNs
Using a VPN with Tor can provide an additional layer of security and anonymity. A VPN encrypts your internet traffic and routes it through a server in a location of your choice, masking your IP address. There are two primary ways to use a VPN with Tor:
- Tor over VPN: Connect to the VPN first, and then launch the Tor Browser. This method encrypts all your traffic before it enters the Tor network, preventing your ISP from seeing that you are using Tor.
- VPN over Tor: Connect to the Tor network first, and then launch the VPN. This method provides additional encryption and can help bypass VPN blocks, but it is more complex to set up and may not provide significant additional security.
Using a VPN with Tor can be beneficial in certain situations, such as when you want to hide your Tor usage from your ISP or when you need to bypass VPN blocks. However, it is important to choose a reputable VPN provider and to understand the potential risks and limitations.
Staying Safe Online
In addition to following the dos and don’ts and using a VPN strategically, here are some additional tips for staying safe online while using Tor:
- Keep your software up to date: Regularly update your operating system, web browser, and other software to protect against security vulnerabilities.
- Use strong passwords: Use strong, unique passwords for all your online accounts to prevent unauthorized access.
- Enable two-factor authentication: Enable two-factor authentication (2FA) whenever possible to add an extra layer of security to your accounts.
- Be careful what you click: Avoid clicking on suspicious links or downloading files from untrusted sources.
- Use a password manager: Use a password manager to store and generate strong passwords securely.
Following these tips can help you stay safe online and protect your privacy while using Tor. Staying vigilant and adopting safe browsing habits are superlatively beneficial to minimize risk.
Troubleshooting
Even with careful use, you may encounter issues with the Tor Browser. Understanding common problems can streamline your troubleshooting process. Addressing these concerns ensures a smoother and more secure anonymous browsing experience.
Common Issues: How to resolve common problems with Tor
- Connection Issues: If Tor Browser fails to connect, check your internet connection, firewall settings, and whether Tor is blocked by your ISP. Restarting the browser or trying a new bridge might resolve the problem.
- Crashing and Freezing: Tor Browser may crash or freeze due to outdated software, excessive cookies and cache, incompatible add-ons, or incorrect bridge settings. Try updating the browser, clearing cookies and cache, disabling add-ons, changing bridge settings, or reinstalling Tor Browser.
- Website Display Problems: Some websites may not display correctly in Tor Browser due to its security settings. Adjust the security level to “Standard” or “Safer”, or disable JavaScript selectively.
- “Tor exited during startup” error: Delete the “Tor” folder inside the Tor Browser installation directory, or reinstall the entire Tor Browser.
- Tor.exe flagged as a trojan: This may happen due to false positive from Windows Defender. Ensure that Windows Defender has not deleted/quarantined Tor.exe, and if so, add Tor.exe to the allowed files.
Regularly updating Tor Browser ensures that any known issues or vulnerabilities are addressed promptly, making it superlatively important to keep your browser current.
Frequently Asked Questions
- Is Tor a legal browser?
Yes, Tor is legal in most parts of the world, and downloading the Tor Browser is a legitimate activity. It’s a privacy tool used for anonymous web surfing. - What is Tor Browser mostly used for?
Tor Browser is mostly used for protecting online privacy, bypassing censorship, and accessing .onion sites on the dark web. It is designed for anonymous web surfing and secure web traffic. - Which browser for dark web?
Tor Browser is the primary browser for accessing the dark web due to its ability to access .onion sites and provide network anonymity. Other browsers may provide access, but lack Tor’s built-in security and anonymity features. - Why do hackers use Tor?
While not exclusively for hackers, Tor provides anonymity that can conceal their online activities, but law enforcement can still track users committing serious crimes. It is superlatively important to use Tor responsibly. - In which country Tor is illegal?
While Tor is legal in most countries, some countries with strict internet censorship may block or restrict its use, though a definitive list is subject to change. Bridges can be used to bypass Tor network blocks.
Conclusion
Tor Browser helps you browse the internet. It hides your IP address and stops trackers. It uses onion routing to guard your identity. It gives you anonymous access to sites, including the dark web. The tool keeps your online life private. It clears your history when you close it. The guide shows you how to install the tool on devices. You use it on Windows, macOS, Linux, and Android. You change your identity with one click. The tool uses bridges to bypass censorship. It stops websites from tracking your actions. It keeps your data safe from harm. The browser uses a strong method to guard your information. It follows clear steps to keep your browsing safe. You use the tool to shield your privacy and block tracking. It stands as a strong guard for online freedom. You enjoy safe web access with this browser. You set your security level to suit your needs. You learn to use each feature. The tool supports people who want full privacy online. It helps you stay safe when you browse and explore. The browser gives you control over your digital life. This tool shows you a way to keep your online world safe.


